Top Cybersecurity Threats and How to Combat Them in 2025
Table of Contents
Top Cybersecurity Threats and How to Combat Them in 2025
Introduction
Cyberattacks aren't just a concern for large corporations. They're a daily threat to businesses of every size. Every day, companies face potential cyberattacks. Just one breach can lead to financial losses, harm your reputation, and put your sensitive information at risk.
That's why safeguarding your business, employees, and customers should be high on your to-do list. The first step to keeping yourself safe is understanding the cyber threats out there.
Hackers are always finding clever new ways to launch attacks, and if you're not aware of the risks, you won't be able to effectively prepare for them. Staying informed empowers you to prevent problems before they arise and ensures your team can respond swiftly if something does go wrong.
While there are numerous types of cyberattacks out there, some are more common than others. In this blog, we'll explore the most frequently encountered cyber threats and share some tips on how to protect your business from them.
Cyberattacks are everywhere now and SMBs are prime targets. Read our blog to learn how MSPs can safeguard your business and keep your operations secure.
Biggest Cybersecurity Threats for 2025
1. AI-powered cyberattacks
Artificial intelligence has been already making waves in many industries and cybercrime is no exception too. We can expect to see more sophisticated AI-driven attacks that can adapt and evade traditional security measures. These attacks may include:
- Intelligent malware that can mutate to avoid detection
- AI-powered phishing campaigns that mimic human behavior
- Automated vulnerability scanning and exploitation
How to combat it?
- Implement cybersecurity solutions powered by AI to monitor and address threats as they arise.
- Consistently update your threat intelligence systems to effectively spot and counteract cyber risks associated with AI.
- Educate your team on how to identify AI-enhanced phishing attempts and other fraudulent strategies.
2. Quantum Computing threats
Quantum computing has tremendous potential for solving complex problems, but it also has its own risks. It can be open to sensitive data vulnerability and poses a significant threat to current cryptographic techniques. Cybercriminals could potentially use this technology to break through our existing security and access sensitive information. Simply put, the better quantum computers get, the more vulnerable our data becomes.
How to combat it?
- Keep yourself updated on post-quantum cryptography to start shifting towards encryption methods that can withstand quantum threats.
- Collaborate with managed IT service providers to evaluate the vulnerabilities present in your current encryption strategies.
- Consider applying a hybrid encryption approach that merges traditional and quantum-resistant methods for enhanced security.
3. Ransomware attacks
Ransomware attacks are continuing to change and remain one of the biggest cybersecurity threats to businesses. It’s becoming more complex, targeting not just data encryption but also exfiltration. Now, cybercriminals are using a tactic called double extortion, where they threaten to release sensitive information if their ransom isn't paid.
This makes it even more important to focus on preventing cyberattacks before they happen. To keep your business safe from these threats, it's important to understand how these attacks are evolving and to put strong protection strategies in place.
- Double extortion happens when cybercriminals encrypt a person's data and threaten to release it publicly unless a ransom is paid.
- Triple extortion goes a step further. Attackers not only demand money from the original victim but also try to extort their clients and partners by threatening to expose sensitive information.
How to combat it?
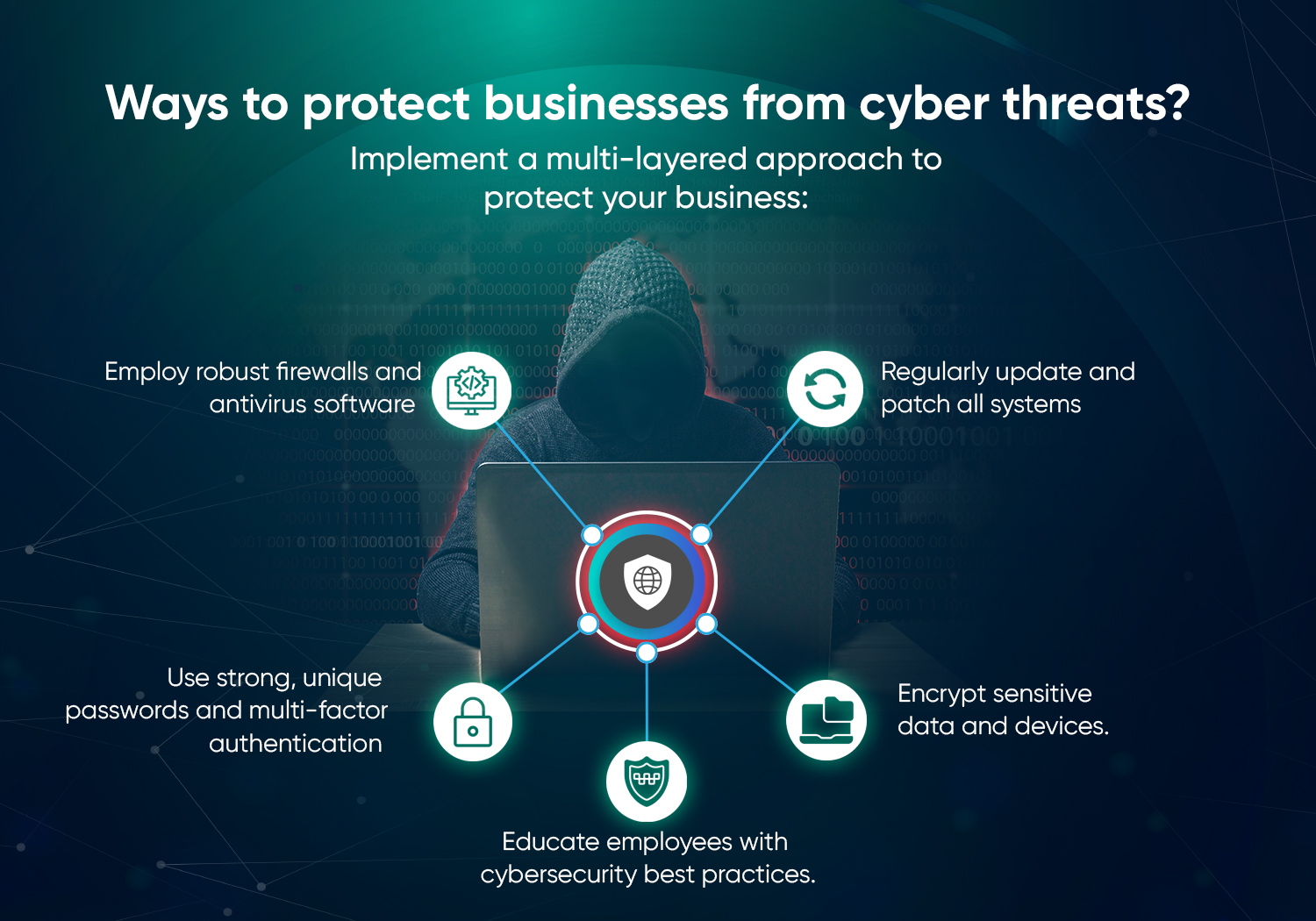
- Use endpoint detection and response (EDR) solutions. These tools can help us catch ransomware and other malicious activity early on before it spreads.
- Make regular backups and be sure to store them offline and encrypted.
- Train your employees in security best practices, especially how to spot and avoid phishing scams.
- Consider partnering with a Managed Security Services Provider (MSSP). They can provide round-the-clock monitoring and a quick response if any issues pop up.

4. Phishing and social engineering scams
Phishing attacks are becoming increasingly sophisticated, and it’s a trend that’s not showing signs of slowing down. Cybercriminals are using deepfakes and AI-generated emails to deceive a wide range of targets, from employees to top executives. These attacks exploit human psychology and vulnerabilities within systems. We can expect to see even more advanced phishing scams that utilize social engineering to outsmart even the most vigilant individuals.
How to combat it?
- Train employees on how to recognize phishing attempts through real-world simulations.
- Implement AI-powered email security solutions that can detect and quarantine phishing emails.
- Adopt multi-factor authentication (MFA) to prevent unauthorized access, even if credentials are compromised.
5. IoT vulnerabilities
Internet of Things (IoT) devices, including security cameras, create more entry points for cybercriminals. While these devices enhance our convenience, they can also represent the weakest links in our security, potentially granting hackers an easy pathway into our networks. With more devices connected to the internet, the avenue for cybercriminals to exploit is huge.
Simply put, an unsecured smart device might expose sensitive data or even disrupt essential operations. In 2025, we predict a slightly upward trend in large-scale attacks aimed at these interconnected IoT systems.
How to combat it?
- To enhance security and safeguard your systems, it’s important to regularly update firmware and apply patches to mitigate potential exploits.
- Consider implementing network segmentation to effectively isolate your IoT devices from critical business systems.
- Strong authentication measures are mandatory. Ensures you use robust passwords and avoid relying on default settings.
6. Cloud security threats
The adoption of cloud services continues to grow in 2025, yet it also opens new doors to security risks. Because of the rise of working remotely and using cloud services, it's more important than ever to focus on keeping our cloud systems secure. Common issues such as misconfiguration, weak access controls, and insecure APIs are among the leading causes of data breaches in cloud environments.
These vulnerabilities can provide cybercriminals with opportunities to infiltrate systems, steal sensitive data, or disrupt vital operations. Hence organizations need to identify these potential weaknesses and implement robust security measures to safeguard their assets.
How to combat it?
- Encrypt data in transit and at rest to protect against unauthorized access.
- Adopt zero-trust security frameworks that limit access based on strict verification processes.
- Monitor cloud environments in real-time with security information and event management (SIEM) tools.
7. Insider threats and data breaches
The security of your data can often be jeopardized by employees within your own organization. Insider threats can arise from anyone with access to your systems, be it employees, contractors, or even partners. Regardless of whether the actions are malicious or accidental, the threat to your data is very real. Whether due to intentional wrongdoing or simple oversight, employees have the potential to compromise sensitive information. Insider threats will remain a significant cybersecurity challenge for businesses across all sectors.
How to combat it?
- Limit access privileges following the principle of least privilege (PoLP).
- Monitor user behavior using behavior analytics tools to detect anomalies.
- Conduct regular security training to educate employees on data protection policies.
A Quick Checklist on Responding to a Cyberattack
If your business falls victim to a cyberattack:
- Isolate affected systems to prevent further spread.
- Notify relevant stakeholders, including employees, customers, and authorities.
- Engage cybersecurity experts to investigate and remediate the breach.
- Review and update security protocols to prevent future incidents.
- Implement additional security measures based on lessons learned.
The need for a robust incident response and disaster recovery plan
Given the increasing complexity and pervasiveness of cyberattacks expected in 2025, your businesses need to stay prepared for potential disruptions. A well-designed incident response and disaster recovery plan not only minimizes downtime but also protects financial stability and brand reputation.
How to build an incident response plan
- Define roles and responsibilities - Assign clear roles to team members responsible for handling cybersecurity incidents.
- Establish communication protocols - Develop internal communication strategies and external stakeholder notification processes.
- Conduct regular tabletop exercises - Simulate cyber incidents to test and refine response strategies.
How to develop a strong disaster recovery plan
- Maintain regular data backups - Ensure frequent backups and rapid restoration capabilities to prevent data loss.
- Identify critical business functions - Determine essential operations and create contingency plans for seamless recovery.
- Test recovery procedures regularly - Conduct periodic testing to validate the effectiveness of recovery strategies and improve response times.
Conclusion
We hope you’ve gained a better understanding of the risks posed by cyber threats. And it's indeed that no business is entirely safe from them. While simple steps, like keeping your software updated and training your employees, can help. Handling cybersecurity can feel like a daunting task. With the help of a managed security service provider, you can get expert monitoring and quick threat responses to keep your business safe.
If you're looking for a reliable security partner, Teceze’s Managed Security Services are here for you. Try and see how you can ensure your business stays protected without the stress of threats and breaches.
 Back to Insights
Back to Insights
 Previous
Previous 