What Is Cyber Resilience? Why It Is Important?
Table of Contents
Important of Cyber Resilience and How Does Work?
It is hard to imagine life in this modern age without information technology. From business experiences such as the sale and purchase of shares to personal encounters such as posting details and photos on social media, information is constantly disseminated around cyberspace. It has allowed society to become more connected, and more prosperous economies. Just as every system comes with risks, however, the security of information in cyberspace is crucial to every business or organization.
The disturbing cyber-attack rate is the reason why companies should be prepared to handle these risks. Moreover, if those companies had better cyber resilience, these attacks could have been managed to deal with.
What is Cyber Resilience?
Cyber resilience is the ability to plan, respond, and recover from cyber-attacks and Data Breaches while continuing to work effectively.
An Enterprise is cyber resilient when it can protect against cyber attacks, provide appropriate risk control for information protection, and ensure continuity of operation during and after cyber incidents.
In recent years, cyber resilience has evolved alongside surface management of threats, as conventional security measures such as Penetration testing and protection questionnaires, are no longer adequate to reduce cyber risk.
Cyber resilience aims to maintain your ability to always deliver goods and services. This may include the ability to restore regular mechanisms, as well as the ability to change or modify mechanisms continuously on an as-needed basis even after regular mechanisms have failed, such as during a crisis or after a security breach.
What are the Four Cyber Resilience Elements?
- Manage and protect – It includes having the ability to identify, analyze, and handle security threats associated with networks and information systems, including those through both third-party and fourth-party vendors.
- Identify and detect – This includes continuous security monitoring and surface management of threats to detect anomalies and possible data breaches and data leaks before any serious damage occurs.
- Respond and recover – This involves adequate incident response planning to ensure continuity of business, even if you are the victim of a cyberattack.
- Govern and assure – The final element is to ensure your cyber resilience program is supervised as usual from the top of your organization and part of your business.
How Does Cyber Resilience Work?
When put into practice, cyber resilience needs to be considered a preventive measure to counteract human error and insecure (and hardware) software. The goal of cyber resilience, therefore, is to aggressively protect the entire Enterprise, taking into account all the vulnerable components in the infrastructure.
Cyber resilience has grown to cover four main components: Threat Protection, Recovery, Adaptability, and Durability.
Threat Protection – The more technology advances, the more cybercrime evolves. Therefore, basic safety won’t help protect the company. What steps should an organization take to guard itself in the event of a threat?
First, the company needs to be safe from targeted Email attacks. Going beyond simple anti-spam and anti-virus software, and incorporating DNS authentication mechanisms into the environment, is important. Do not create a void in email protection under the presumption that the IT department has specific security products from third-party vendors. Invest in a single approach that can respond to the changing world of cyberattacks.
The best choice for your company could be an Endpoint Detection and Response (EDR) solution. EDR tools operate by tracking endpoint and network events and storing the information in a central database where further analysis, identification, review, reporting, and alerting are carried out. Detection is enabled by using analytical tools that classify activities that can boost the overall security status by deflecting specific attacks and enabling early detection of ongoing assaults.
Recoverability – Recoverability is the ability of a firm to return to normal business functions following an attack. A well-designed attack on Ransomware can encrypt all your data, forcing you to either pay the attackers a ransom or lose the data. Should provide frequent and comprehensive backups on a separate network of your data which can be used to recover any wiped data.
Compared to a fire drill, running a data breach scenario simulation will help to improve your cyber resilience. Go through all the steps your organization will have to take in case of an infringement, i.e. how the IT team will escalate a potential security infringement, communicate with clients, inform stakeholders, and inform law enforcement agencies.
Adaptability – Since attackers are continually finding new ways of escaping detection and creating new planes of attack, the enterprise-wide network must adapt and evolve to protect against potential threats.
To prevent attacks, the security department must be able to detect a security breach and react to it quickly. Furthermore, administrator monitoring needs to be built in to detect users who are infected or at risk.
Adaptability is an integral part of cyber resilience. The company would be a step closer to a more cyber-resilient environment if the security department had user awareness education, could detect threats in actuality, and implemented automation to eliminate those threats.
Durability – The durability of the company-wide cyber resilience is determined not just by the IT infrastructure but also by the capacity of the organization to operate effectively after a cyberattack. The cyber resilience durability aspect will improve with the IT team’s daily updates and device enhancements.
Cyber resilience’s primary aim is to protect the entire business. As the consequences of a data breach can be technical, social, and financial, prioritizing cyber resilience by integrating business operations with IT is imperative for every business.
Why Cyber Resilience is Important?
Traditional protection measures are not sufficient; that’s why Cyber Resilience has grown over the last few years. It is now reasonable to assume that attackers will eventually gain access to various computer systems and that organizations should start preparing to work on strategies to resist these cybercrimes.
Strategies for cyber resilience provide a range of advantages before, during, and after cyber attacks:
- To maintain the integrity of an organization – When a company lacks cyber resilience, it is difficult to monitor the harm caused by cybercriminals. Cyber resilience protects a company from public criticism, administrative penalties, and sudden revenue cuts, or worse, business losses.
- Having regulatory and judicial specifications – Meeting legal requirements also offers a valuable advantage in incorporating cyber resilience into an Enterprise. Compliance with the laws will improve the organization’s protection framework, such as the Network and Information Systems (NIS) Directive, which requires each entity to ‘take reasonable protection measures and inform the relevant national authority of serious incidents’. There is also the General Data Protection Regulation (GDPR) which promises to protect data privacy and restructure the way organisations handle the privacy of their data.
- Enhanced protection of the systems – Cyber resilience helps to respond to an attack and withstand it. It can also help the company build an IT governance strategy, enhance safety and security across sensitive assets, strengthen data protection efforts, prevent natural disaster impacts, and reduce human error.
- More trust in the customer and vendor ecosystem – Over the past decade, and rightly so, a lot of focus has been put on vendor risk management and third-party risk management frames. Confidence is a two-way street though. Before asking your vendors to, your company must have cyber resilience strategies in place. Unless your company has poor cyber resilience, it may harm your clients and vendors’ credibility.
- Improving the work culture and the process from the inside – Each employee of any company must strive for data protection and other IT infrastructures. If people are motivated at their organization to take protection seriously, confidential information and physical properties are more likely to be in safe hands. The company will be improving the right security actions within each department and reducing human errors that reveal confidential data.
- Reducing the losses – No matter how strong an organization’s IT protection is, the fact is no company is immune to cyberattacks. According to estimates, financial loss from data breaches is more than one hundred thousand for small and medium-sized businesses. That is more than a million for major organizations. Furthermore, if a security breach succeeds, it will harm the credibility of the company in the industry as well. It can also heighten financial harm. When a company has cyber resilience, it will mitigate the impact of the attack, and so will the financial losses.
How Teceze Can Improve the Cyber Resilience of Your Organization?
Teceze is a leading global consultancy in the field of cyber risk and privacy management. We counsel multinational organizations on their most important problems and propose cost-saving and risk-reducing approaches based on best practices and international frameworks. Just like we have been supporting hundreds of other groups around the world, so we can benefit.
The only way to protect what you’ve worked hard to build is to be vigilant when it comes to cybersecurity. If you’d like to know more about how your business can benefit from managed services, just give us a call, we are here to help.
Cyber resilience is important because traditional security measures are no longer enough to ensure adequate information security, data.
 Back to Insights
Back to Insights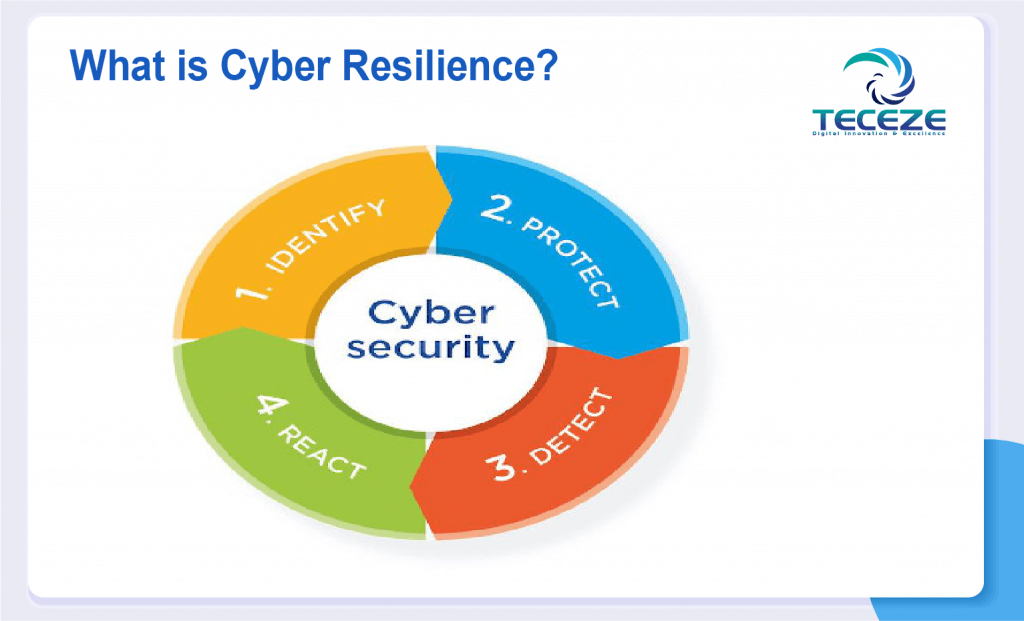
 Previous
Previous 