Why Penetration testing is important?
Table of Contents
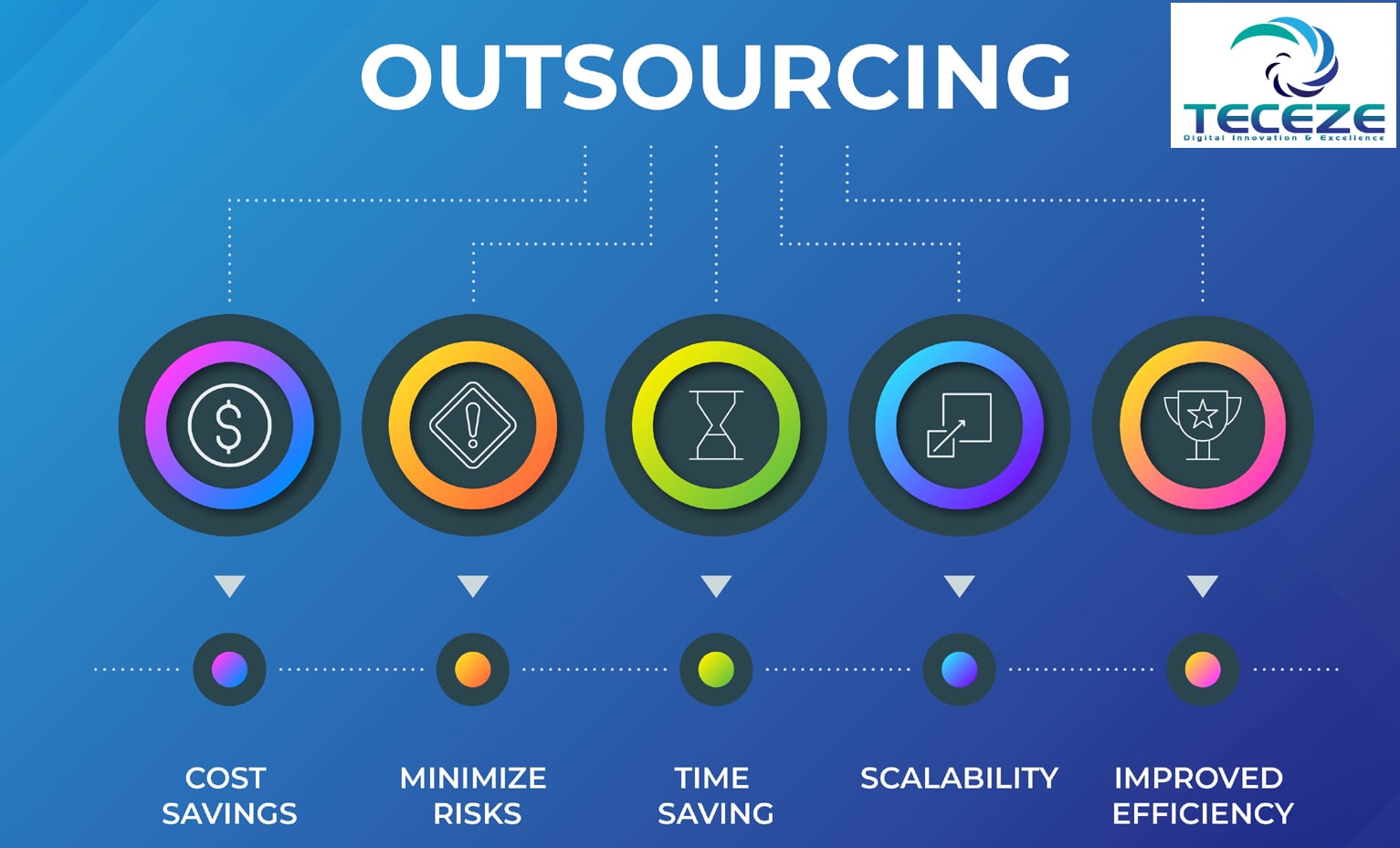
Penetration testing (pen testing or ethical hacking) is a security procedure that involves analyzing your computer system's software for vulnerabilities and susceptibility to attacks such as hacking and cyber-attacks.



 Previous
Previous